Customer Cache Data Protection#

Overview#
Customer Cache Data Protection enables encryption of the content and derived data cache services for Omniverse on DGX Cloud.
This document follows this Microsoft step by step guide: Encrypt managed disks with cross-tenant customer-managed keys.
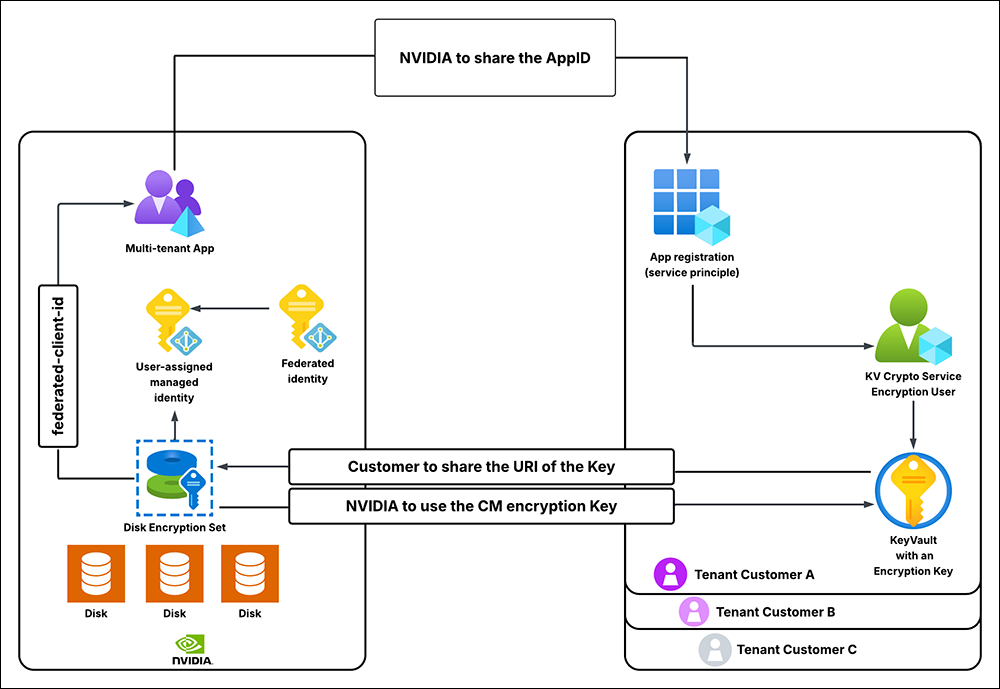
Solution Diagram#
Scope and Limitations#
It takes a considerable amount of time (up to one hour per Microsoft Azure guidance) for key status changes to propagate. This means if the customer revokes / deletes / restores the key on their side, it might take the aforementioned amount of time for the caching microservices to stop / restart working.
The Azure Key Vault must be configured with Soft-Delete and Purge-Protection. This is an Azure requirement.
The Azure Key Vault must exist in the same Azure location as the Omniverse on DGX Cloud caching services. NVIDIA will provide guidance of the location to spin up the Key Vault instance. This is an Azure requirement.
Getting Started#
Register the Application#
Register the application in your Microsoft Azure tenant. Using the Azure CLI, execute the following command:
az ad sp create --id <custom_app_name>
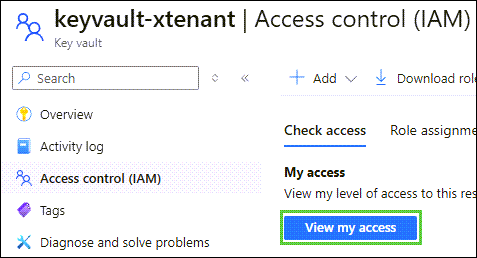
Verify Key Vault Crypto Officer Role Assignment#
Click Access control (IAM), followed by View my access:
In the menu, filter roles by Key Vault Crypto Officer:
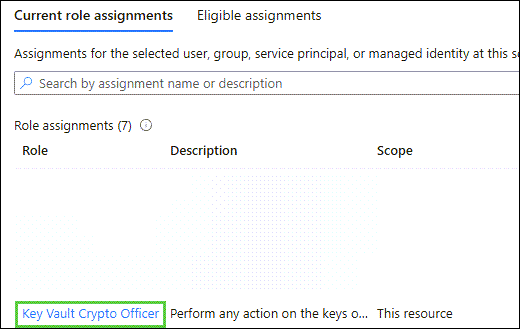
Confirm your account has the Key Vault Crypto Officer Role assigned to it. If it does, skip the next section.
Assign the Key Vault Secrets Officer Role#
Note
Skip this section if you already have the Key Vault Secrets Officer role assigned to your account.
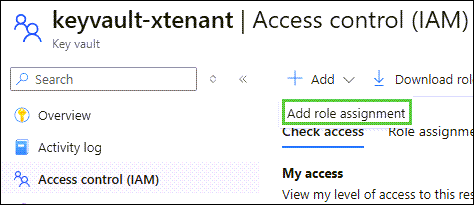
Click Access control (IAM), Add, followed by Add role assignment:
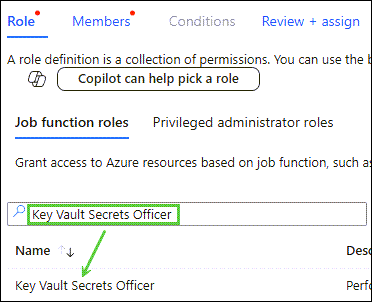
Search for Key Vault Secrets Officer and click Key Vault Secrets Officer. Confirm the selected role is Key Vault Secrets Officer, followed by Next at the bottom of the window:
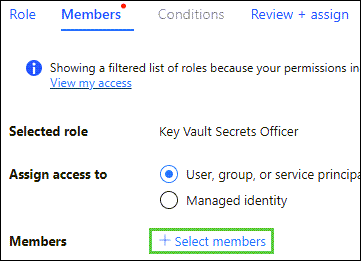
At the Members window, click + Select members:
Click your account from the list of members to choose from, followed by Select and then Review + Assign twice:

Add a Key Vault Crypto Service Encryption User Role to the Service Principle#
Click Access control (IAM), Add, followed by Add role assignment:

Filter by Key Vault Crypto Service Encryption User, click the role, followed by Next:
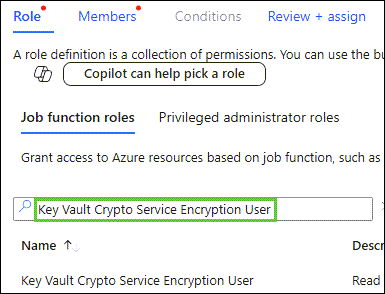
At the Members window, click + Select members:
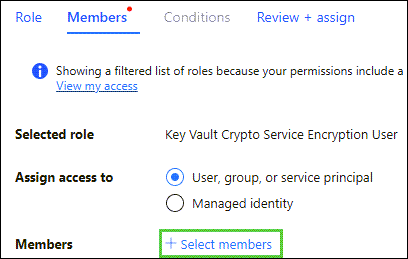
Click your account from the list of members to choose from, followed by Select and then Review + Assign twice:

Create a New Key Vault Key#
Note
Skip this section if using an existing key.
In the Objects menu, click Keys, followed by Generate/Import:
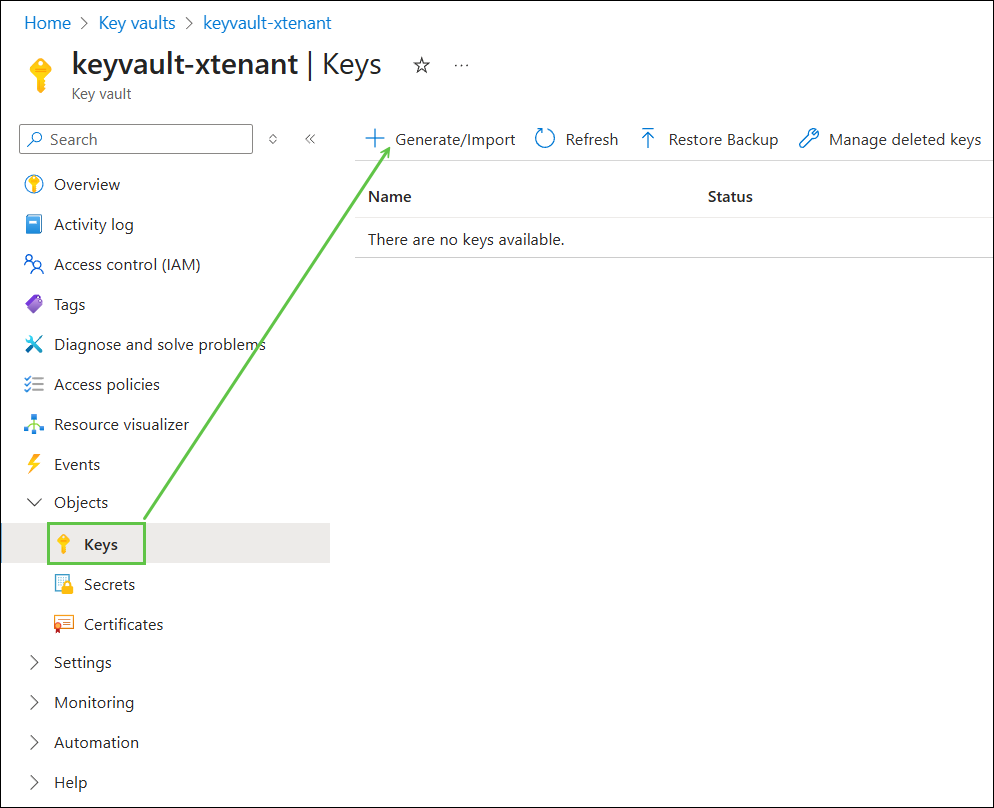
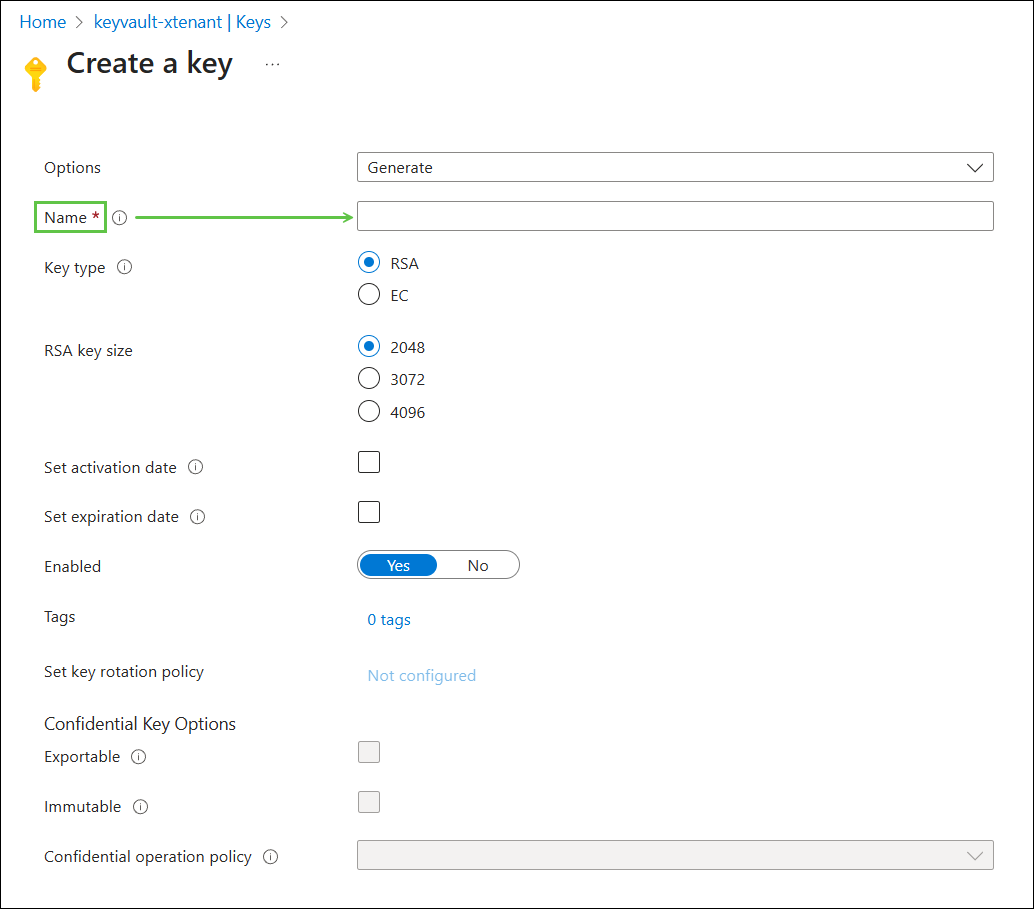
Following your security policies, enter a preferred name, followed by Create:
Information to send to NVIDIA#
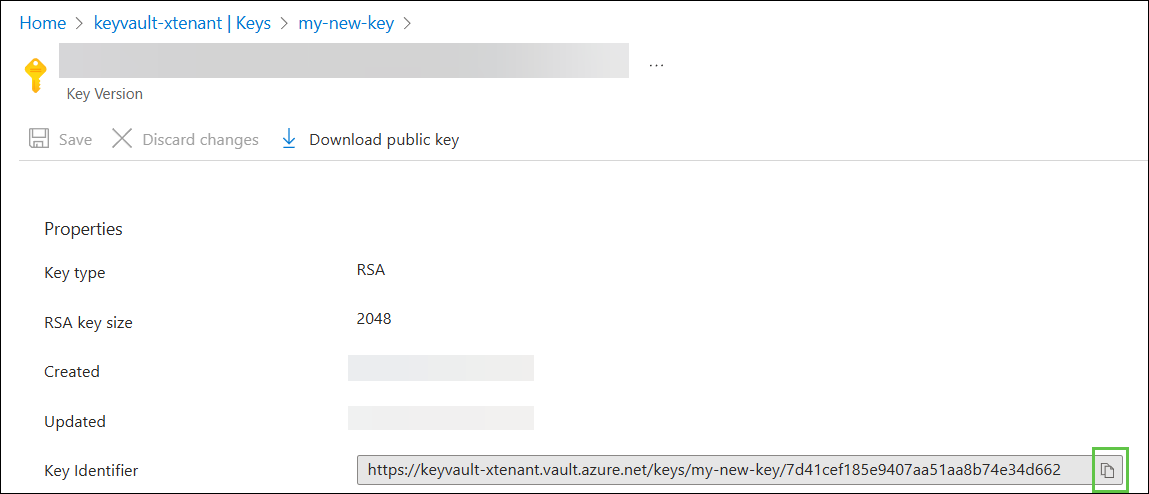
Full URL of the Key Identifier#
Click the key you intend NVIDIA to encrypt their volumes with, then click Current Version of the key:
Use the Copy to Clipboard button to copy the Key Identifier and share it with NVIDIA: