Integration using OpenID Connect#
Integration using OpenID Connect is the preferred solution. With OpenID Connect, the NVIDIA identity federation system is at the client side of the integration (Relaying Party) while your identity management system is at the server side of the integration (OpenID Provider).
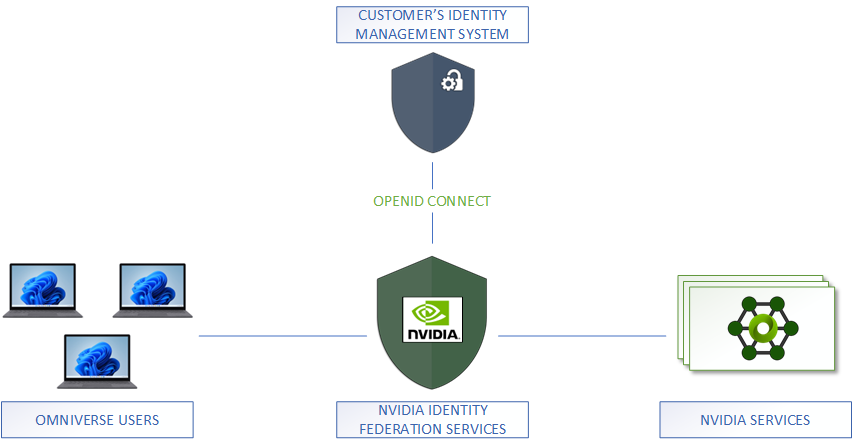
The interactions between NVIDIA and your identity management system follow the authorization code flow specified in section 3.1 of OpenID Connect Core 1.0.
Token Endpoint#
The token endpoint of your identity management system must conform to the operations specified in section 3.1.3 of OpenID Connect Core 1.0.
Support for the client authentication method client_secret_basic or client_secret_post is required. Refer to section 9 of OpenID Connect Core 1.0
for the corresponding definitions.
Access to the token endpoint cannot be restricted on a per client source IP Address basis. The NVIDIA identity federation system uses dynamic IP Addresses to call the token endpoint.
Identity Token#
The format of the identity token must be compliant with section 2 of OpenID Connect Core 1.0. The identity token payload should contain at least the following information about the user:
Claim |
Description |
|---|---|
sub |
REQUIRED – Unique identifier assigned by your identity management system to the user. |
preferred_username |
REQUIRED – Short name that identifies the account used to log in. |
REQUIRED – Email address of the user. |
|
email_verified |
RECOMMENDED – Email address verification status. |
name |
RECOMMENDED – Full name of the user. |
Note
NVIDIA can accommodate the use of different claims in the place of preferred_username. Examples
of standard OpenID Connect claims that may be used for the same function include name*, nickname,
or given_name. Alternatively, also non-standard claims specific to your identity management system may be accommodated.
The identity token payload may also contain a claim to convey the group memberships of the user. See the Support for user groups for details.
User Info Endpoint#
Support for the user info endpoint is optional. If your identity management system does not expose the user info endpoint, the NVIDIA identity federation system can extract the user information directly from the identity token payload.
When supported, the user info endpoint must conform to the operations specified in section 5.3 of OpenID Connect Core 1.0.
Access to the user info endpoint cannot be restricted on a per client source IP Address basis. The NVIDIA identity federation system uses dynamic IP Addresses to call the token endpoint.
Transport Layer Security#
All endpoints exposed by your identity management system must require the use of SSL/TLS and have a server certificate traceable to a Certificate Authority (CA) recognized by all major web browsers (e.g., Chrome, Safari, Firefox). Use of self-signed certificates are not allowable in any phase of the integration. The domain name used for the endpoints must also be owned by your company.
Client Credentials#
To enable the integration, you need to assign a client identifier and its associated client secret to NVIDIA. The client must be enabled to use the following two redirect URIs (also known as callback URLs):
https://stg.login.nvidia.com/callback/redirecthttps://login.nvidia.com/callback/redirect**
The first URL is used by NVIDIA to perform integration tests. The second URL above is used in production.
Email Domains#
The user experience at login starts with a request to enter the work email address. The NVIDIA identity federation system uses the domain part of the email address to determine the identity provider that should authenticate the user. For this reason, you need to provide the list of email domains in use at your company.
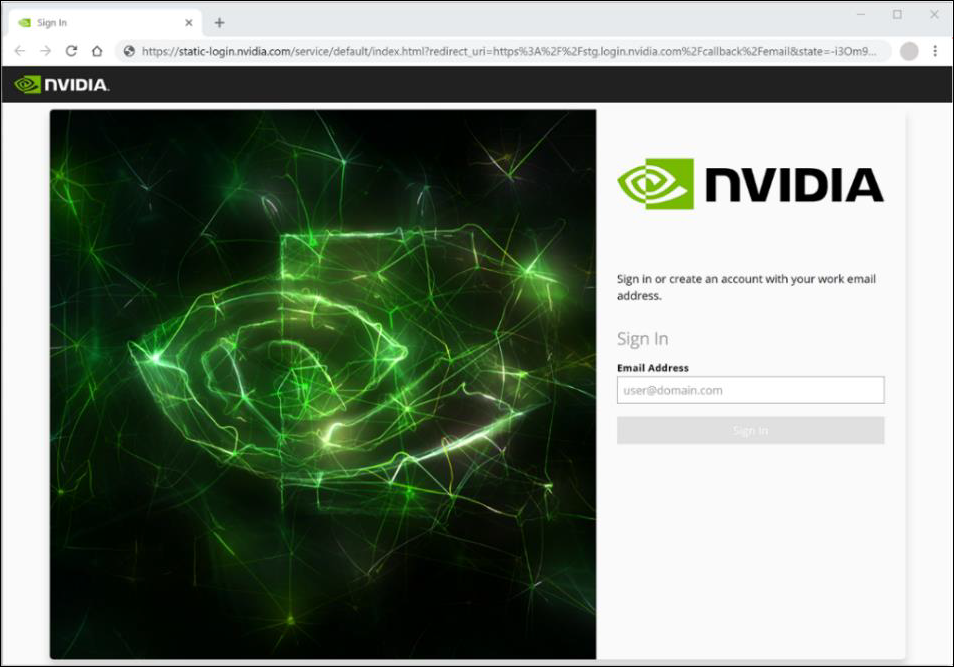
After the user has entered the email address, the NVIDIA identity federation system redirects the browser to the authorization endpoint of your identity management system. The authorization request is composed so it includes the login_hint parameter with a value equal to the user email address. For example:
login_hint=user@example.com <mailto:login_hint%3Duser@example.com>
To ensure the best possible user experience, your identity management system should use the login_hint value to pre-populate the login form served to the user. This is not a strict requirement; however, if the identity management system ignores the login hint, the users may have to re-enter their username twice.
Support for User Groups#
If your identity management system supports groups, the integration with NVIDIA can be set up so the NVIDIA identity federation system receives the group memberships of your employees when they log in. This capability is critical to enable fine grained user authorization decisions at the NVIDIA side. For example, you can manage access to specific NVIDIA services for your employees by only managing their group memberships.
There is no standardized way to return group memberships via OpenID Connect. The following sections describe mechanisms that can be used to fill this gap. .. _identity-token-1:
Identity Token#
Your identity management system may include one claim with the group memberships of the user in the identity token payload. For example, claim groups may be used to return the list of groups as an array of strings.
User Info Endpoint#
Your identity management system may include the user group memberships in the response returned by the user info endpoint. This approach may be used in alternative or in addition to the inclusion of group memberships in the identity token.
Other Endpoints#
Your identity management system may expose other endpoints to retrieve the user group memberships. Examples include the /memberOf endpoint of the Microsoft Graph APIs, the /Me endpoint of the SCIM APIs, or other solution specific endpoints.
Information to be Provided to NVIDIA#
The following table specifies the information that NVIDIA needs to set up the integration:
Info |
Comments |
Full URL of the OpenID Connect provider configuration endpoint |
In general, the URL ends with |
Authorization scopes that NVIDIA should request |
NVIDIA will include these scopes in the authorization requests, (e.g., scope=openid profile email) |
Client credentials that NVIDIA can use for the integration |
Refer to the Email Domains section for more details. |
Test account that NVIDIA can use to verify the integration |
If possible, please provide the username and password of one test account. Otherwise, please provide a sample identity token payload and/or userinfo response body so NVDIA can determine the claims that your system uses to return information about the user |
List of email domains in use at your company |
Refer to the Client Credentials section for more details. |
Description of how NVIDIA can obtain user groups memberships |
Only if groups are used. Refer to the Support for User Groups section for more details. |