SSL/TLS Configuration#
All communications between Client Applications and Nucleus use a combination of WebSockets and HTTP which allows SSL/TLS can be used to secure the traffic.
Omniverse Clients support both SSL/TLS and non-TLS connections; they detect (and favor) SSL/TLS automatically.
An Enterprise Nucleus Server, however, does not itself provide SSL/TLS termination. This means that even though your deployment can be configured with SSL/TLS, Nucleus itself will not “talk” SSL/TLS: it will still be listening on series of ports, opened as insecure HTTP or WebSocket endpoints.
We rely on a reverse proxy for SSL/TLS connections. Clients connect to the proxy via SSL/TLS, and it forwards their requests to Nucleus over regular, non-secure connections. We call this proxy an Ingress Router.
Note
We recommend that all clients connect directly to your Enterprise Nucleus Server, as routing has only be validated against our Ingress Router. External proxies are not supported.
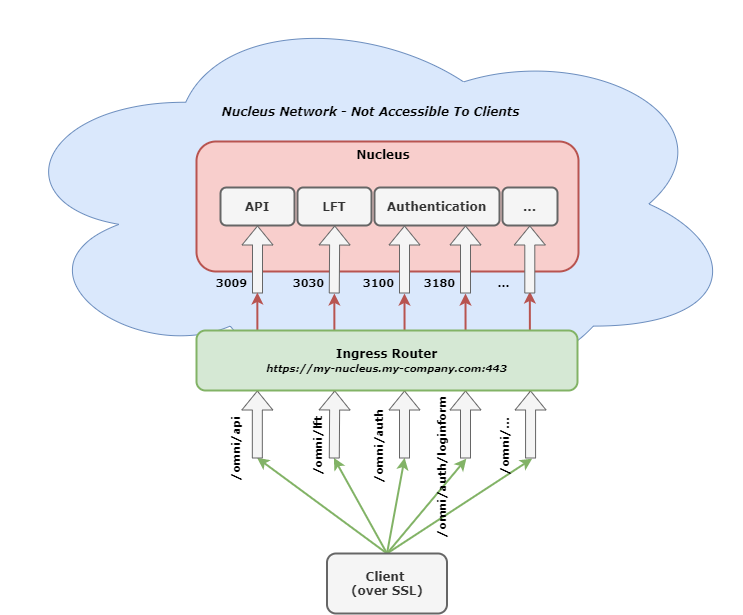
Non-TLS Clients connect to various Nucleus Components directly - on their ports (e.g., 3009, 3030). With
SSL/TLS however, Clients connect to a host - i.e., https://my-nucleus.my-company.com - which is where the Ingress Router is configured.
The Ingress Router examines the path of the request - and routes (reverse-proxies) a Client based on that path. This is known as Path-based Routing (PBR).
If a non-SSL Client talks to the Nucleus API for example, it would open
a connection to my-nucleus-host.my-company.com, port 3009.
With SSL/TLS (and PBR), it will instead connect to https://my-nucleus.my-company.com/omni/api. The host portion of this URL will lead it to the SSL/TLS
termination point (Ingress Router), and path (/omni/api) will indicate to the Ingress Router that the request should be reverse-proxied to Nucleus’s port 3009.
(Reference the diagram above on how paths correlate to ports.)
Setting up Nucleus with SSL/TLS#
In order to enable SSL/TLS for Nucleus, the following items are needed:
Configure the appropriate network topology
Configure a reverse proxy to act as an Ingress Router
Configure the Nucleus Base Stack to be aware of the Ingress Router
Network Topology#
Given that Nucleus itself does not terminate SSL/TLS, if strong security is desired, Nucleus should be placed in a network that is not directly accessible by Clients.
A host to run the Ingress Router should be able to freely access Nucleus, and be accessible to Clients on ports TCP 80 and TCP 443.
Configuring Ingress Router#
Any reverse proxy can act as an Ingress Router, provided it supports WebSockets, HTTP, path/port redirection, and SSL/TLS. We recommend using NGINX as it’s lightweight and easy to configure.
To make setup easier, we ship a sample NGINX configuration file with the Enterprise Nucleus Server artifact. This configuration can be used as is with minor customization (URLs and IP Addresses), however it can also serve as a guide to configure alternative options as needed.
Additionally, we include an Ingress Router Docker container if you prefer to run it on the Enterprise Nucleus Server itself.
Click the appropriate link below to learn more:
Warning
Omniverse Clients (Apps and Connectors) only support certificates with validated trust chains. Self-signed certificates or certificates with non-matching hostname’s will not work properly with Omniverse Clients and will fail without warning.
To properly configure a Nucleus Enterprise Server in a secured environment, certificates provided by a well-known Certificate Authority (CA) are required. Single domain certificates, multiple domain (SAN) certificates, and wildcard (*) certificates are fully supported.
If your Enterprise relies on an internal PKI (Public Key Infrastructure), this is supported providing the proper trust certificates are deployed to the workstations that connect to the Enterprise Nucleus Server.